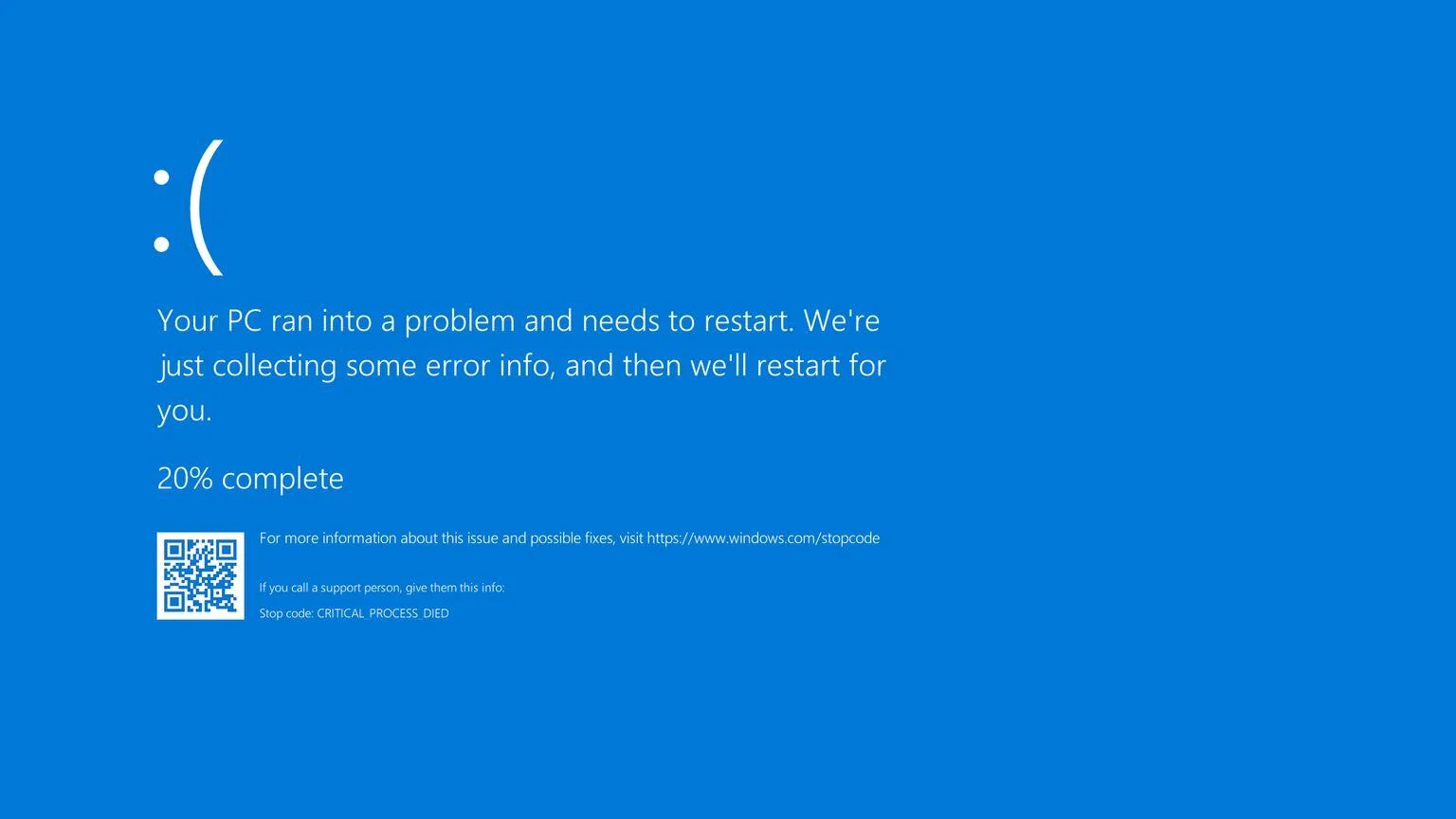
INCIDENT RESPONSE
IRAAS
SERVICE
SERVICE
On-site incident response coordination from qualified & experienced team.
Effective incident management will minimize damage to systems and data, reducing recovery time and costs, controlling damage and maintaining brand reputation.
RELIABILITY
On-site IR including dispatching qualified engineer 24/7.
EXPERIENCE
Over +12 years of intervention for public and private entities.
FAST
SLA remote under 30 min.
FORENSIC
Best tooling to investigate, detect, discover, contain, and eradicate a compromised environment.
RELIABILITY
On-site IR including dispatching qualified engineers 24/7.
EXPERIENCE
Over +12 years of intervention for public and private entities.
FAST
SLA remote
under 30 min.
FORENSIC
Best tooling to investigate, detect, discover, contain, and eradicate a compromised environment.

Our Priority: Getting Your Business Back on Track
An incident can seriously disrupt your activity, even cause it to stop.
It is essential that specialists take action as quickly as possible in order to contain the infection. Accustomed to these emergency response situations, our experts work in conjunction with your IT teams to implement a business activity continuity and resumption plan.
In order to prevent an incident from happening again, it will be of prime importance to address your vulnerabilities and reinforce your protection for the long term.
In order to prevent an incident from happening again, it will be of prime importance to address your vulnerabilities and reinforce your protection for the long term.
The structured incident response process and methodologies employed by ZENDATA involve close collaboration with law enforcement agencies, commonly referred to as the 'cyber police,' across multiple cities. This approach has facilitated international coalition building, collaborative efforts, synchronization, and the sharing of critical data. Additionally, ZENDATA proudly maintains a partnership with the Interpol cybercrime intelligence unit.
An emergency response is conducted according to the following model:
1. Contain the infection.
2. Investigate the source of infection and define the Ioc and Ioa.
3. Block the input vector.
4. Eradicate the attack.
5. Deploy provisional safeguards.
6. Implement a business resumption plan.
7. Reporting and debriefing.
2. Investigate the source of infection and define the Ioc and Ioa.
3. Block the input vector.
4. Eradicate the attack.
5. Deploy provisional safeguards.
6. Implement a business resumption plan.
7. Reporting and debriefing.
Define the situation
and context
Determine the
investigation’s scope
and gain access
Conduct the
Investigation
Submit the detailed
report
OUR Conduct OF Investigation
We regularly plays a role in digital investigations, which are analyzed in detail by a certified cybersecurity engineer using recognized vanguard solutions. A detailed report is provided at the conclusion of the investigation. Here are two main types of missions:
- Investigation into the presence of malwareThis investigation allows us to verify the presence, intent, and infection sources of malicious code.
- Investigation into fraudulent use.The purpose of this investigation is to analyze the fraudulent actions of an employee on a firm’s computer system.
IRaaS
SERVICE
Defining the criteria for incidents and their initiators is crucial for ensuring business continuity. ZENDATA's experts conduct thorough investigations, extracting valuable threat data admissible in court. We perform legal scientific inquiries and offer in-house forensic and malware analysis with experienced engineers.
Our comprehensive investigation reports include threat assessments suitable for criminal investigations and law enforcement purposes. These reports detail our investigative steps, threat analysis, collected IoC & IoA, temporary mitigation, initial access findings, and recommendations.
INCLUDED
Our IRaaS service includes, but is not limited to:
• Incident response coordination and management
• On-site Incident Response
• Attack investigation
• Breach containment
• Initial access discovery
• Persistence & backdoor removal
• Ransomware and blackmail negotiation service
• Analysis of assets (endpoints, servers, network equipment, mobile equipment, etc.) that may have been infected
• Post-incident reporting and debriefing including future remediations
• On-site and remote forensic analysis
• Emergency BCP/BRP implementation & execution
• Deployment of temporary security tools
• On-demand file analysis
• Incident response coordination and management
• On-site Incident Response
• Attack investigation
• Breach containment
• Initial access discovery
• Persistence & backdoor removal
• Ransomware and blackmail negotiation service
• Analysis of assets (endpoints, servers, network equipment, mobile equipment, etc.) that may have been infected
• Post-incident reporting and debriefing including future remediations
• On-site and remote forensic analysis
• Emergency BCP/BRP implementation & execution
• Deployment of temporary security tools
• On-demand file analysis