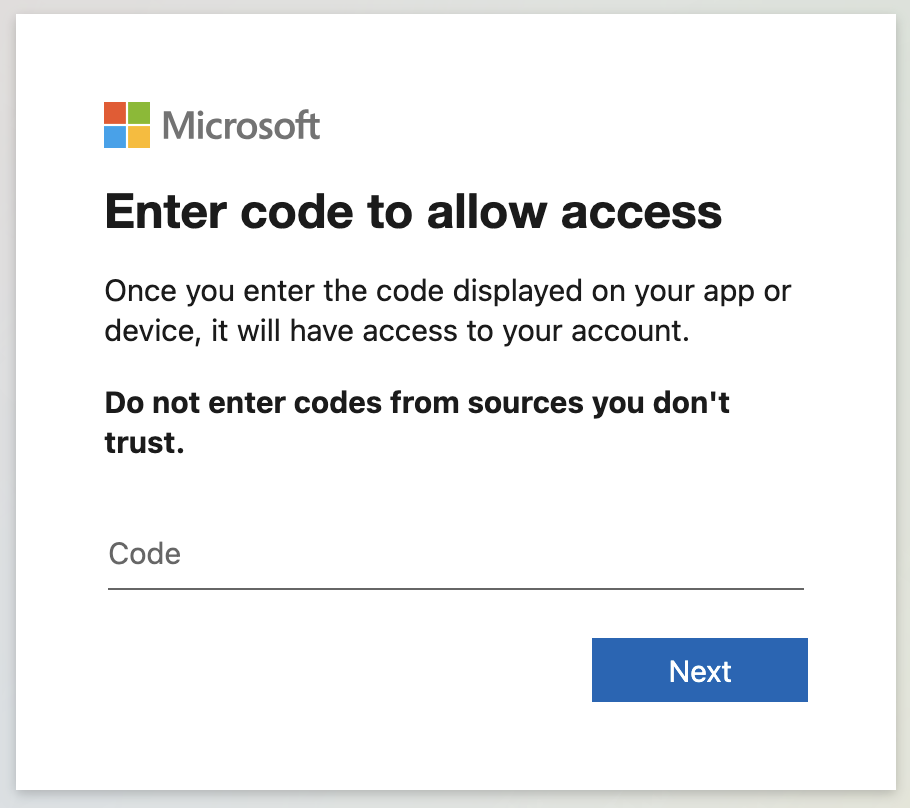
Hackers have found an effective way to bypass Microsoft 365 authentication by abusing the device code flow—a mechanism meant for logging in devices without traditional input methods. This attack is concerning because it exploits user confusion rather than technical vulnerabilities, making social engineering the real weapon here.
How it works:
The attackers impersonate high-profile entities (government agencies, research institutions) and initiate conversations via messaging apps. They then send a device authorization code, tricking the user into entering it on a legitimate Microsoft page—unknowingly granting full access to their account.
Why it works:
The authentication process is too opaque for users—many don’t realize they are granting access to an external device rather than simply authenticating themselves. The attackers leverage the natural trust people place in familiar workflows like joining Teams meetings or logging into cloud services.
Expert Analysis – what needs to change?
- Microsoft needs clearer UX warnings—users should understand what they are granting access to.
- SOC need to monitor authentication logs—device code-based logins should be closely tracked.
- Users must be trained to recognize social engineering attacks—especially when codes and login flows are involved.
At the end of the day, authentication is a plumbing system too complex for most users to fully grasp. If users don’t understand what they’re approving, they can’t defend against these attacks—which is exactly what threat actors are betting on.
Microsoft and security teams need to take ownership of clarity and visibility in authentication, or this attack method won’t be the last of its kind.
This brings back the eternal debate of efficiency vs. security…
Read the full article here.